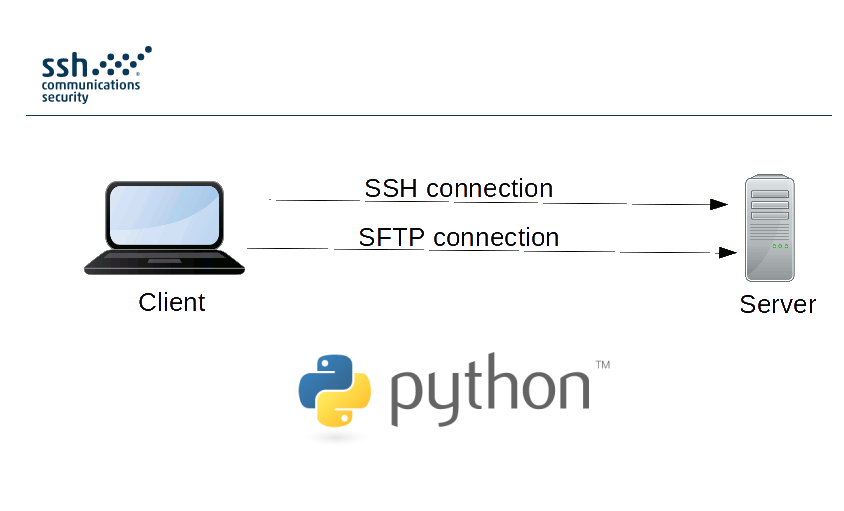
In computing, the SSH File Transfer Protocol (also Secure File Transfer Protocol, or SFTP) is a network protocol that provides file access, file transfer, and file management over any reliable data stream.
To automate tasks that create and manage files on a Secure File Transfer Protocol (SFTP) server using the Secure Shell (SSH) protocol, you can create automated integration workflows by using Azure Logic Apps and the SFTP-SSH connector. SFTP is a network protocol that provides file access, file transfer, and file management over any reliable data stream.
In this article. To automate tasks that create and manage files on a Secure File Transfer Protocol (SFTP) server using the Secure Shell (SSH) protocol, you can create automated integration workflows by using Azure Logic Apps and the SFTP-SSH connector. SFTP is a network protocol that provides file access, file transfer, and file management over any reliable data stream. SSH and SFTP Clients. Here are some SSH clients that we recommend for connecting to remote machines: Macintosh. Mac OSX 10.x has built in SSH and SFTP as part of the Un.x command line tools. Penn State has obtained a site license from SSH, Inc. The fully licensed Windows client. A secure flexible SSH client with SFTP file transfer and rock-solid emulations that is suitable for developers, administrators, or deployment across the enterprise. It includes the industry standard SSH protocols to secure terminal session data across insecure environments such as the internet.
Here are some example tasks you can automate:
- Monitor when files are added or changed.
- Get, create, copy, rename, update, list, and delete files.
- Create folders.
- Get file content and metadata.
- Extract archives to folders.
In your workflow, you can use a trigger that monitors events on your SFTP server and makes output available to other actions. You can then use actions to perform various tasks on your SFTP server. You can also include other actions that use the output from SFTP-SSH actions. For example, if you regularly retrieve files from your SFTP server, you can send email alerts about those files and their content using the Office 365 Outlook connector or Outlook.com connector. If you're new to logic apps, review What is Azure Logic Apps?
For differences between the SFTP-SSH connector and the SFTP connector, review the Compare SFTP-SSH versus SFTP section later in this topic.
Limits
The SFTP-SSH connector currently doesn't support these SFTP servers:
- IBM DataPower
- MessageWay
- OpenText Secure MFT
- OpenText GXS
SFTP-SSH actions that support chunking can handle files up to 1 GB, while SFTP-SSH actions that don't support chunking can handle files up to 50 MB. The default chunk size is 15 MB. However, this size can dynamically change, starting from 5 MB and gradually increasing to the 50-MB maximum. Dynamic sizing is based on factors such as network latency, server response time, and so on.
Note
For logic apps in an integration service environment (ISE),this connector's ISE-labeled version requires chunking to use the ISE message limits instead.
You can override this adaptive behavior when you specify a constant chunk size to use instead. This size can range from 5 MB to 50 MB. For example, suppose you have a 45-MB file and a network that can that support that file size without latency. Adaptive chunking results in several calls, rather that one call. To reduce the number of calls, you can try setting a 50-MB chunk size. In different scenario, if your logic app is timing out, for example, when using 15-MB chunks, you can try reducing the size to 5 MB.
Chunk size is associated with a connection. This attribute means you can use the same connection for both actions that support chunking and actions that don't support chunking. In this case, the chunk size for actions that don't support chunking ranges from 5 MB to 50 MB. This table shows which SFTP-SSH actions support chunking:
Action Chunking support Override chunk size support Copy file No Not applicable Create file Yes Yes Create folder Not applicable Not applicable Delete file Not applicable Not applicable Extract archive to folder Not applicable Not applicable Get file content Yes Yes Get file content using path Yes Yes Get file metadata Not applicable Not applicable Get file metadata using path Not applicable Not applicable List files in folder Not applicable Not applicable Rename file Not applicable Not applicable Update file No Not applicable SFTP-SSH triggers don't support message chunking. When requesting file content, triggers select only files that are 15 MB or smaller. To get files larger than 15 MB, follow this pattern instead:
Use an SFTP-SSH trigger that returns only file properties. These triggers have names that include the description, (properties only).
Follow the trigger with the SFTP-SSH Get file content action. This action reads the complete file and implicitly uses message chunking.
Compare SFTP-SSH versus SFTP
The following list describes key SFTP-SSH capabilities that differ from the SFTP connector:
Uses the SSH.NET library, which is an open-source Secure Shell (SSH) library that supports .NET.
Provides the Create folder action, which creates a folder at the specified path on the SFTP server.
Provides the Rename file action, which renames a file on the SFTP server.
Caches the connection to SFTP server for up to 1 hour. This capability improves performance and reduces how often the connector tries connecting to the server. To set the duration for this caching behavior, edit the ClientAliveInterval property in the SSH configuration on your SFTP server.
Prerequisites
An Azure subscription. If you don't have an Azure subscription, sign up for a free Azure account.
Your SFTP server address and account credentials, so your workflow can access your SFTP account. You also need access to an SSH private key and the SSH private key password. To upload large files using chunking, you need both read and write access for the root folder on your SFTP server. Otherwise, you get a '401 Unauthorized' error.
The SFTP-SSH connector supports both private key authentication and password authentication. However, the SFTP-SSH connector supports only these private key formats, algorithms, and fingerprints:
- Private key formats: RSA (Rivest Shamir Adleman) and DSA (Digital Signature Algorithm) keys in both OpenSSH and ssh.com formats. If your private key is in PuTTY (.ppk) file format, first convert the key to the OpenSSH (.pem) file format.
- Encryption algorithms: DES-EDE3-CBC, DES-EDE3-CFB, DES-CBC, AES-128-CBC, AES-192-CBC, and AES-256-CBC
- Fingerprint: MD5
After you add an SFTP-SSH trigger or action to your workflow, you have to provide connection information for your SFTP server. When you provide your SSH private key for this connection, don't manually enter or edit the key, which might cause the connection to fail. Instead, make sure that you copy the key from your SSH private key file, and paste that key into the connection details. For more information, see the Connect to SFTP with SSH section later this article.
Basic knowledge about how to create logic apps
The logic app workflow where you want to access your SFTP account. To start with an SFTP-SSH trigger, create a blank logic app workflow. To use an SFTP-SSH action, start your workflow with another trigger, for example, the Recurrence trigger.
How SFTP-SSH triggers work
Polling behavior
SFTP-SSH triggers poll the SFTP file system and look for any file that changed since the last poll. Some tools let you preserve the timestamp when the files change. In these cases, you have to disable this feature so your trigger can work. Here are some common settings:
| SFTP client | Action |
|---|---|
| Winscp | Go to Options > Preferences > Transfer > Edit > Preserve timestamp > Disable |
| FileZilla | Go to Transfer > Preserve timestamps of transferred files > Disable |
When a trigger finds a new file, the trigger checks that the new file is complete, and not partially written. For example, a file might have changes in progress when the trigger checks the file server. To avoid returning a partially written file, the trigger notes the timestamp for the file that has recent changes, but doesn't immediately return that file. The trigger returns the file only when polling the server again. Sometimes, this behavior might cause a delay that is up to twice the trigger's polling interval.
Trigger recurrence shift and drift
Connection-based triggers where you need to create a connection first, such as the SFTP-SSH trigger, differ from built-in triggers that run natively in Azure Logic Apps, such as the Recurrence trigger. In recurring connection-based triggers, the recurrence schedule isn't the only driver that controls execution, and the time zone only determines the initial start time. Subsequent runs depend on the recurrence schedule, the last trigger execution, and other factors that might cause run times to drift or produce unexpected behavior. For example, unexpected behavior can include failure to maintain the specified schedule when daylight saving time (DST) starts and ends. To make sure that the recurrence time doesn't shift when DST takes effect, manually adjust the recurrence. That way, your workflow continues to run at the expected time. Otherwise, the start time shifts one hour forward when DST starts and one hour backward when DST ends. For more information, see Recurrence for connection-based triggers.
Convert PuTTY-based key to OpenSSH
The PuTTY format and OpenSSH format use different file name extensions. The PuTTY format uses the .ppk, or PuTTY Private Key, file name extension. The OpenSSH format uses the .pem, or Privacy Enhanced Mail, file name extension. If your private key is in PuTTY format, and you have to use OpenSSH format, first convert the key to the OpenSSH format by following these steps:
Unix-based OS
If you don't have the PuTTY tools installed on your system, do that now, for example:
sudo apt-get install -y puttyRun this command, which creates a file that you can use with the SFTP-SSH connector:
puttygen <path-to-private-key-file-in-PuTTY-format> -O private-openssh -o <path-to-private-key-file-in-OpenSSH-format>For example:
puttygen /tmp/sftp/my-private-key-putty.ppk -O private-openssh -o /tmp/sftp/my-private-key-openssh.pem
Windows OS
If you haven't done so already, download the latest PuTTY Generator (puttygen.exe) tool, and then launch the tool.
On this screen, select Load.
Browse to your private key file in PuTTY format, and select Open.
From the Conversions menu, select Export OpenSSH key.
Save the private key file with the
.pemfile name extension.
Considerations

This section describes considerations to review when you use this connector's triggers and actions.
Use different SFTP folders for file upload and processing
On your SFTP server, use separate folders for storing uploaded files and for the trigger to monitor those files for processing. Otherwise, the trigger won't fire and behaves unpredictably, for example, skipping a random number of files that the trigger processes. However, this requirement means that you need a way to move files between those folders.
If this trigger problem happens, remove the files from the folder that the trigger monitors, and use a different folder to store the uploaded files.
Create file
To create a file on your SFTP server, you can use the SFTP-SSH Create file action. When this action creates the file, the Logic Apps service also automatically calls your SFTP server to get the file's metadata. However, if you move the newly created file before the Logic Apps service can make the call to get the metadata, you get a 404 error message, 'A reference was made to a file or folder which does not exist'. To skip reading the file's metadata after file creation, follow the steps to add and set the Get all file metadata property to No.
Connect to SFTP with SSH
When you add a trigger or action that connects to a service or system for the first time, the Logic App Designer prompts you to create a connection by providing the necessary information, which varies based on the connection, for example:
The name that you want to use for the new connection
The name for the system or server
Your user or account credentials
The authentication type to use
Sign in to the Azure portal, and open your logic app in Logic App Designer, if not open already.
For blank logic apps, in the search box, enter
sftp sshas your filter. Under the triggers list, select the trigger you want.-or-
For existing logic apps, under the last step where you want to add an action, select New step. In the search box, enter
sftp sshas your filter. Under the actions list, select the action you want.To add an action between steps, move your pointer over the arrow between steps. Select the plus sign (+) that appears, and then select Add an action.
Provide the necessary details for your connection.
Important
When you enter your SSH private key in the SSH private key property, follow these additional steps, which helpmake sure you provide the complete and correct value for this property. An invalid key causes the connection to fail.
Although you can use any text editor, here are sample steps that show how to correctly copy and paste your key by using Notepad.exe as an example.
Open your SSH private key file in a text editor. These steps use Notepad as the example.
On the Notepad Edit menu, select Select All.
Select Edit > Copy.
In the SFTP-SSH trigger or action, paste the complete copied key in the SSH private key property, which supports multiple lines. Don't manually enter or edit the key.
After you finish entering the connection details, select Create.
Now provide the necessary details for your selected trigger or action and continue building your logic app's workflow.
Override chunk size
To override the default adaptive behavior that chunking uses, you can specify a constant chunk size from 5 MB to 50 MB.
In the action's upper-right corner, select the ellipses button (...), and then select Settings.
Under Content Transfer, in the Chunk size property, enter an integer value from
5to50, for example:After you finish, select Done.
Examples
SFTP - SSH trigger: When a file is added or modified
This trigger starts a workflow when a file is added or changed on an SFTP server. As example follow-up actions, the workflow can use a condition to check whether the file content meets specified criteria. If the content meets the condition, the Get file content SFTP-SSH action can get the content, and then another SFTP-SSH action can put that file in a different folder on the SFTP server.
Enterprise example: You can use this trigger to monitor an SFTP folder for new files that represent customer orders. You can then use an SFTP-SSH action such as Get file content so you get the order's contents for further processing and store that order in an orders database.
SFTP - SSH action: Get file content using path
This action gets the content from a file on an SFTP server by specifying the file path. So for example, you can add the trigger from the previous example and a condition that the file's content must meet. If the condition is true, the action that gets the content can run.
Troubleshoot problems
This section describes possible solutions to common errors or problems.
504 error: 'A connection attempt failed because the connected party did not properly respond after a period of time, or established connection failed because connected host has failed to respond' or 'Request to the SFTP server has taken more than '00:00:30' seconds'
This error can happen when your logic app can't successfully establish a connection with the SFTP server. There might be different reasons for this problem, so try these troubleshooting options:
The connection timeout is 20 seconds. Check that your SFTP server has good performance and intermediate devices, such as firewalls, aren't adding overhead.
If you have a firewall set up, make sure that you add the Managed connector IP addresses to the approved list. To find the IP addresses for your logic app's region, see Limits and configuration for Azure Logic Apps.
If this error happens intermittently, change the Retry policy setting on the SFTP-SSH action to a retry count higher than the default four retries.
Check whether SFTP server puts a limit on the number of connections from each IP address. If a limit exists, you might have to limit the number of concurrent logic app instances.
To reduce connection establishment cost, in the SSH configuration for your SFTP server, increase the ClientAliveInterval property to around one hour.
Review the SFTP server log to check whether the request from logic app reached the SFTP server. To get more information about the connectivity problem, you can also run a network trace on your firewall and your SFTP server.
404 error: 'A reference was made to a file or folder which does not exist'
This error can happen when your workflow creates a file on your SFTP server with the SFTP-SSH Create file action, but immediately moves that file before the Logic Apps service can get the file's metadata. When your workflow runs the Create file action, the Logic Apps service automatically calls your SFTP server to get the file's metadata. However, if your logic app moves the file, the Logic Apps service can no longer find the file so you get the 404 error message.
If you can't avoid or delay moving the file, you can skip reading the file's metadata after file creation instead by following these steps:
In the Create file action, open the Add new parameter list, select the Get all file metadata property, and set the value to No.
If you need this file metadata later, you can use the Get file metadata action.
Connector reference
For more technical details about this connector, such as triggers, actions, and limits as described by the connector's Swagger file, see the connector's reference page.
Note
For logic apps in an integration service environment (ISE),this connector's ISE-labeled version require chunking to use the ISE message limits instead.
Next steps
- Learn about other Logic Apps connectors
In computing, the SSH File Transfer Protocol (also Secure File Transfer Protocol, or SFTP) is a network protocol that provides file access, file transfer, and file management over any reliable data stream. It was designed by the Internet Engineering Task Force (IETF) as an extension of the Secure Shell protocol (SSH) version 2.0 to provide secure file transfer capabilities. The IETF Internet Draft states that, even though this protocol is described in the context of the SSH-2 protocol, it could be used in a number of different applications, such as secure file transfer over Transport Layer Security (TLS) and transfer of management information in VPN applications.
This protocol assumes that it is run over a secure channel, such as SSH, that the server has already authenticated the client, and that the identity of the client user is available to the protocol.
Capabilities[edit]
Compared to the SCP protocol, which only allows file transfers, the SFTP protocol allows for a range of operations on remote files which make it more like a remote file system protocol. An SFTP client's extra capabilities include resuming interrupted transfers, directory listings, and remote file removal.[1]
SFTP attempts to be more platform-independent than SCP; with SCP, for instance, the expansion of wildcards specified by the client is up to the server, whereas SFTP's design avoids this problem. While SCP is most frequently implemented on Unix platforms, SFTP servers are commonly available on most platforms. The file transfer is fast in SCP when compared to the SFTP protocol due to the back and forth nature of SFTP protocol. In SFTP, the file transfer can be easily terminated without terminating a session like other mechanisms do.
Ssh And Sftp Client For Mac
SFTP is not FTP run over SSH, but rather a new protocol designed from the ground up by the IETF SECSH working group. It is sometimes confused with Simple File Transfer Protocol.[1]
The protocol itself does not provide authentication and security; it expects the underlying protocol to secure this. SFTP is most often used as subsystem of SSH protocol version 2 implementations, having been designed by the same working group. It is possible, however, to run it over SSH-1 (and some implementations support this) or other data streams. Running an SFTP server over SSH-1 is not platform-independent as SSH-1 does not support the concept of subsystems. An SFTP client willing to connect to an SSH-1 server needs to know the path to the SFTP server binary on the server side.
Uploaded files may be associated with their basic attributes, such as time stamps. This is an advantage over the common FTP protocol.
History and development[edit]
The Internet Engineering Task Force (IETF) working group 'Secsh' that was responsible for the development of the Secure Shell version 2 protocol (RFC 4251) also attempted to draft an extension of that standard for secure file transfer functionality. Internet Drafts were created that successively revised the protocol into new versions.[2] The software industry began to implement various versions of the protocol before the drafts were standardized. As development work progressed, the scope of the Secsh File Transfer project expanded to include file access and file management. Eventually, development stalled as some committee members began to view SFTP as a file system protocol, not just a file access or file transfer protocol, which places it beyond the purview of the working group.[3] After a seven-year hiatus, in 2013 an attempt was made to restart work on SFTP using the version 3 draft as the baseline.[4]
Versions 0–2[edit]
Prior to the IETF's involvement, SFTP was a proprietary protocol of SSH Communications Security, designed by Tatu Ylönen with assistance from Sami Lehtinen in 1997.[5] Differences between versions 0–2 and version 3 are enumerated upon in section 10 of draft-ietf-secsh-filexfer-02.
Version 3[edit]
At the outset of the IETF Secure Shell File Transfer project, the Secsh group stated that its objective of SSH File Transfer Protocol was to provide a secure file transfer functionality over any reliable data stream, and to be the standard file transfer protocol for use with the SSH-2 protocol.
Drafts 00–02 of the IETF Internet Draft define successive revisions of version 3 of the SFTP protocol.
Version 4[edit]
Ssh.net Sftp Client
Drafts 03–04 of the IETF Internet Draft define version 4 of the protocol.
Version 5[edit]
Draft 05 of the IETF Internet Draft defines version 5 of the protocol.
Version 6[edit]
Drafts 06–13 of the IETF Internet Draft define successive revisions of version 6 of the protocol.
Software[edit]
SFTP client[edit]
The term SFTP can also refer to Secure file transfer program, a command-lineprogram that implements the client part of this protocol. As an example, the sftp program supplied with OpenSSH implements this.[6]
Some implementations of the scpprogram support both the SFTP and SCP protocols to perform file transfers, depending on what the server supports.
SFTP server[edit]
Some FTP server implementations implement the SFTP protocol; however, outside of dedicated file servers, SFTP protocol support is usually provided by an SSH server implementation, as it shares the default port of 22 with other SSH services. SFTP implementations may include an SSH protocol implementation to leverage integration of SSH connection details with preexisting FTP server access controls, where an alternative SSH server is tolerable or where alternative ports may be used. An SSH-2 server which supports subsystems may be leveraged to keep a uniform SSH implementation while enhancing access controls with third party software, at the cost of fine-grained integration with connection details, and SSH-1 compatibility.
SFTP proxy[edit]
It is difficult to control SFTP transfers on security devices at the network perimeter. There are standard tools for logging FTP transactions, like TIS fwtk or SUSE FTP proxy, but SFTP is encrypted, rendering traditional proxies ineffective for controlling SFTP traffic.
There are some tools that implement man-in-the-middle for SSH which also feature SFTP control. Examples of such a tool are Shell Control Box from Balabit[7] and CryptoAuditor from SSH Communications Security[8] (the original developer of the Secure Shell protocol) which provides functions such as SFTP transaction logging and logging of the actual data transmitted on the wire.
See also[edit]
- Lsh—a GNU SSH-2 and SFTP server for Unix-like OSes
- SSHFS—Mounting remote filesystem using SFTP and SSH
References[edit]
- ^ abBarrett, Daniel; Silverman, Richard E. (2001), SSH, The Secure Shell: The Definitive Guide, Cambridge: O'Reilly, ISBN0-596-00011-1
- ^'Secsh Status Pages'. Tools.ietf.org. Retrieved 2012-08-20.
- ^'ietf.secsh—Formal consultation prior to closing the secsh working group—msg#00010—Recent Discussion'. Osdir.com. 2006-08-14. Archived from the original on 2012-03-20. Retrieved 2012-08-20.
- ^'SSH File Transfer Protocol—draft-moonesamy-secsh-filexfer-00'. Gmane.org. 2013-07-12.
- ^ftp://ftp.ietf.org/ietf-mail-archive/secsh/2012-09.mail
- ^'OpenBSD manual page for the 'sftp' command: 'See Also' section'. OpenBSD.org. Retrieved 2018-02-04.
- ^'Record SSH/RDP/Citrix into Audit Trail—Activity Monitoring Device'. Balabit.com. Retrieved 2012-08-20.
- ^'Privileged Access Control and Monitoring'. SSH.com. Retrieved 2014-11-25.
External links[edit]
- Chrooted SFTP with Public Key Authentication – Integrating SFTP into FreeBSD production servers using the public key cryptography approach
